- Setting up your victim application, databases and lab
- Attacking a simple injection with information Schema
- Automating your injections with python and beautiful soup
- Dealing with various web encoding in Python and PHP
- Bypassing LoadFile Size restrictions and automating it
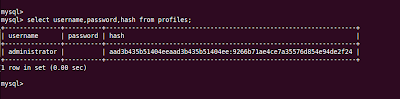
- Decrypting sensitive data via PHP and Python interactions
- As always me rambling about stupid nonsense :P FTW
Part 2 of Mysql covers the topic of injecting a simple SQL injection example. Starts out slow then combines techniques and moves into more advanced topics. Prior to attempting this lesson make sure you have watched the videos in the previous blog or understand both SQL and basic python coding. I will show how to automate the injection process via python utilizing simple HTML processing abilities of beautiful soup. I will cover many python libraries for encoding data and calling web based applications. I also talk about how to deal with encrypted data and methods of enumerating files and folders looking for possible implementation issues and attack points to decrypt sensitive data via PHP/Python interaction with whats available on the server. This is the 2nd part of a 3 part series on MySQL for attacking web applications.
Files Needed:
Lab FilesBT5
Video Lesson:
Whats Next:
PHP source code analysisRecoding PHP applications to fix SQLi